WEB题部分
1.CTF入门级题目
题目给出源码,下载下来
使用%00截断ereg函数,同时不影响strpos函数
得到flag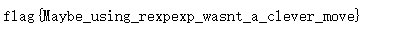
2.曲奇
http://ctf1.shiyanbar.com/shian-quqi/index.php?line=&file=a2V5LnR4dA==
其中有两个参数 line 和 file ,可以发现file参数后的值经过了base64编码,解码后发现是key.txt。尝试修改line的值,但是没有东西显示,于是开始修改file的参数为index.php 的base64编码,通过更改line的值逐行读出源码
得知当cookie的值等于li_lr_480可以访问thisis_flag.php,于是修改file的值为thisis_flag.php的base64编码,并修改cookie的值,访问后直接爆出flag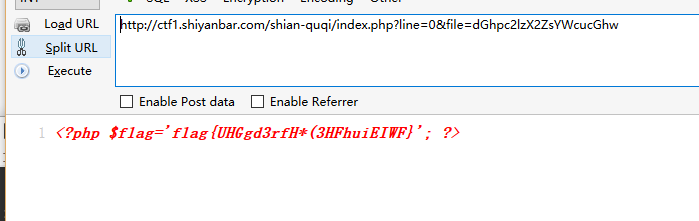
3.类型
|
|
直接看源码,x1 可以等于任意字符串,x2[x21]为任意数组,x2[x22]长度为2,第一个元素为数组,第二个元素为0.
x3的为比较md5的值,查看15562的md5码第八位至二十四位发现位0e+数字的组合,0e在比较的时候会将其视作为科学计数法,所以无论0e后面是什么,0的多少次方还是0,所以py爆破一波。
部分符合条件的字符串及MD5
构造payload
|
|
4.登录
|
|
提示是密码是一个五位数字,同时存在验证码,py一波
爆破出密码 00315,登录即送flag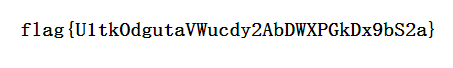
5.Admin
阅读一下源码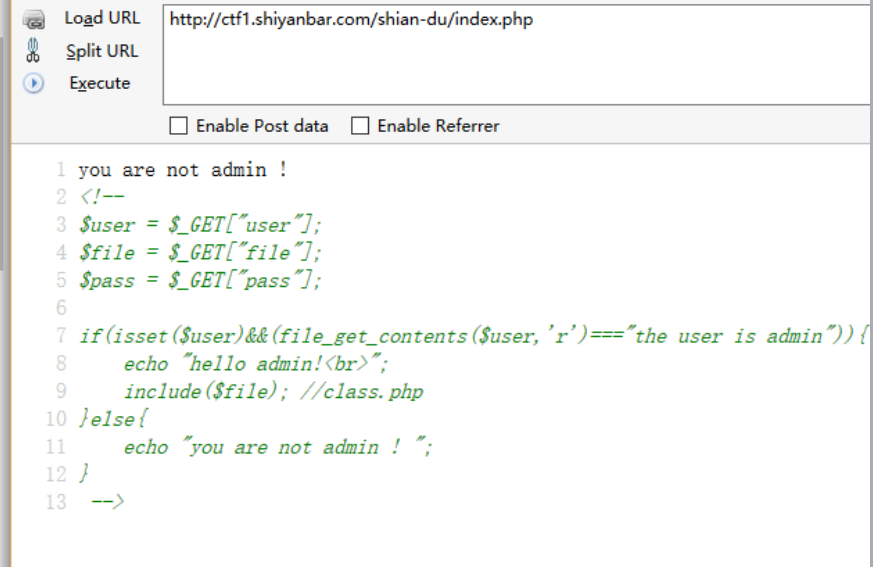
构造php封装协议 php://input 成功绕过第一步过滤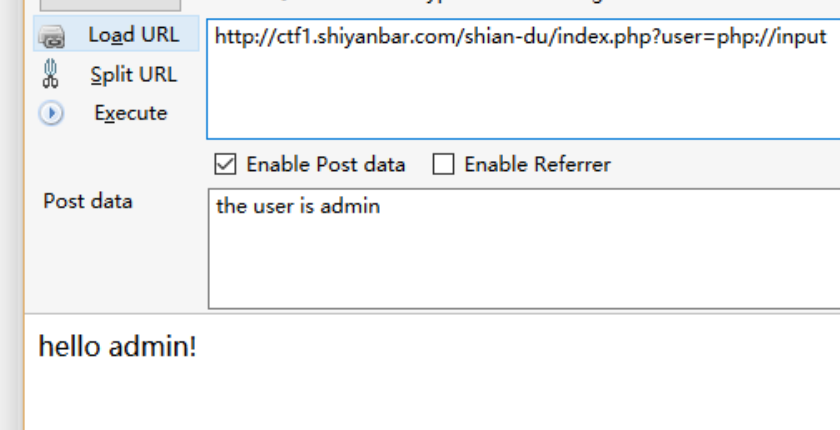
然后构造php://filter 输出base64编码的文件
将输出的index.php 解码得到
接着读取class.php,解码得
构造php反序列化读取fla9.php文件
通过php反序列化漏洞,调用Read函数输出f1a9.php